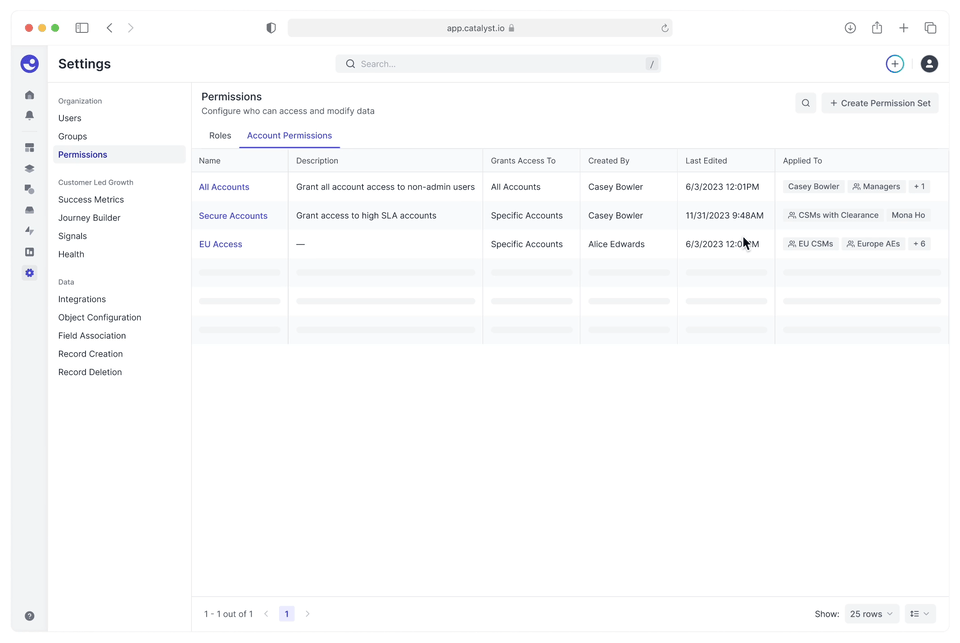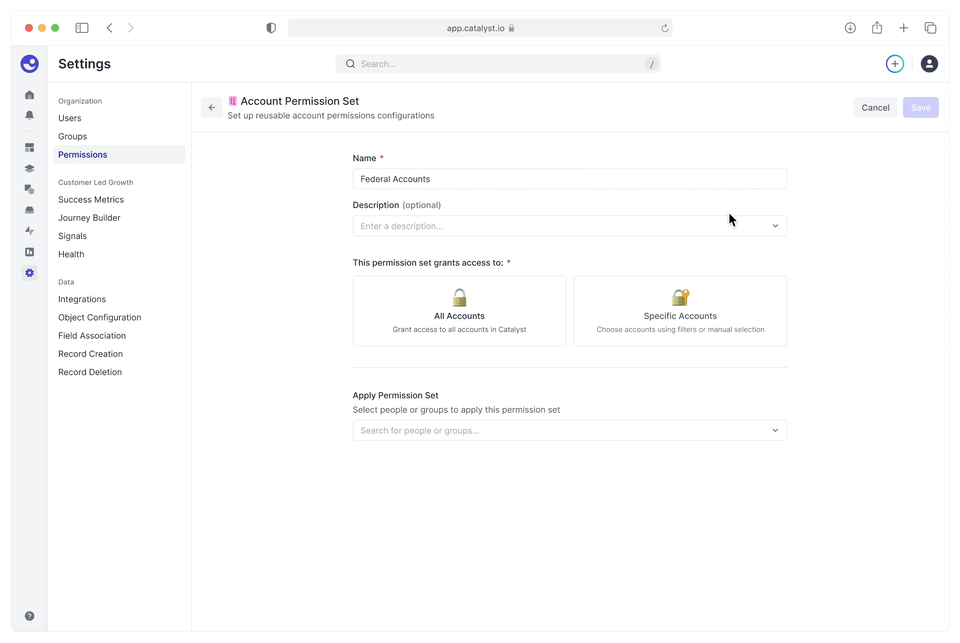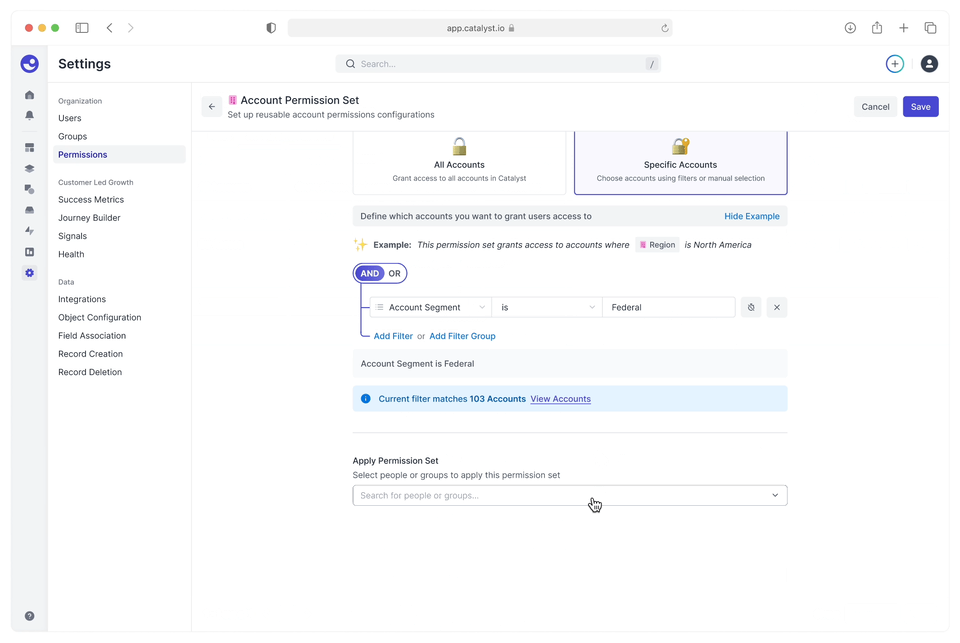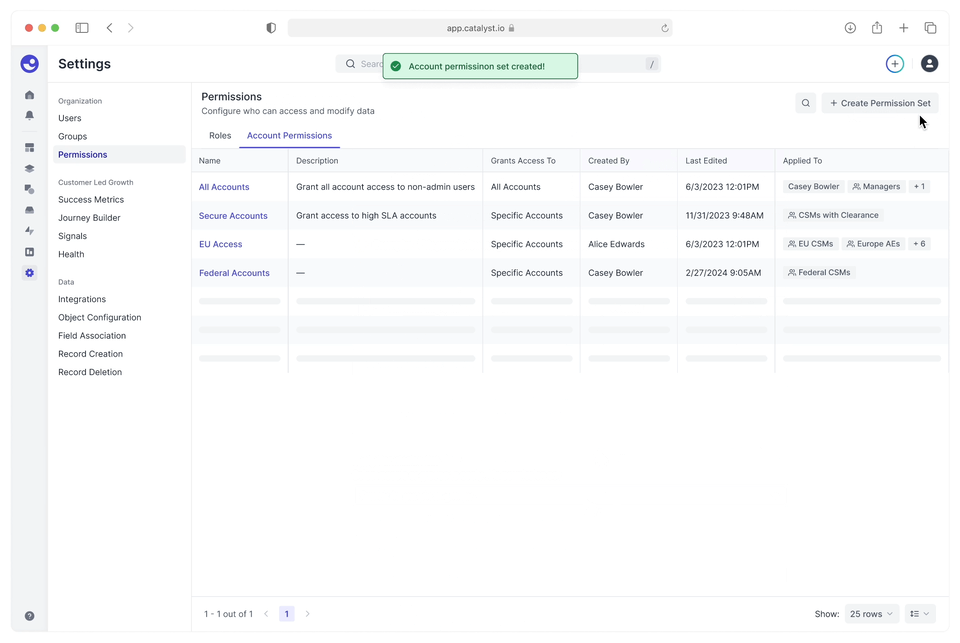
The flow to create an account permission set — granting users or user groups access to accounts as defined by a filter.
Catalyst’s main organizational objects are accounts, the user’s customers, brought in via Salesforce. Previously, the app could only operate in a fully open access model — any user in an organization could see any account. Various customers and prospects over the years had asked for a more secure, account-based permissions system.
We set out to deliver this key feature, prioritizing a quick, low-lift configuration experience for Catalyst admins.

The flow to create an account permission set — granting users or user groups access to accounts as defined by a filter.
My PM and I got on a call with three different customers to dig into their needs and ask questions, including:
Why is it essential for your organization to restrict access to accounts and account-based data?
How do you logically separate groups of users currently?
Do you have any workarounds that you've used to hack this feature using Catalyst's existing functionality?
From these calls, we defined the following primary use cases:
Lock down sensitive accounts
One customer has a segment of federal accounts, which must be restricted to CSMs with security clearance. Currently, they can't even bring these accounts into Catalyst because there's no way to limit access to just the federal team.
Eyes on your own paper
Some customers simply want their CSMs to focus on their own work, without the information overload of seeing all accounts in the system. They might want to divide their users into teams, and limit their account access to just their team's accounts.
I set up a cross-functional design thinking workshop for my team to start noodling on permissions frustrations, questions, and solutions.



The following was an exploration of our draft mode feature — allowing admins to configure permissions "in draft" to avoid interruption to their team's daily workflows.

Not shown in between these two steps: countless critique meetings with the design and product teams, sessions with engineers to nail down technical capabilities, validation calls with internal stakeholders and Beta customers, several rounds of VQA and refinement, and lots and lots of me-time in Figma.

A version which allows account ownership to be defined, granting users access to only their own accounts.

Account not found screen, shown if a user ever lands on a permalink for an account they don't have access to.

Turning on restricted account access in draft mode.

Account permissions listing on a user group, showing which permission sets they have been granted access to alongside an audit of past permissions.
The release of this feature unblocked one enterprise deal and two high-value renewals, resulting in:
In positively impacted revenue *
* Exact amount obscured for privacy reasons
We are currently monitoring permission set creation and editing metrics to ensure lasting usability — we track our metrics and user behavior patterns in Mixpanel and Fullstory.

Another key metric I plan on observing as we add more enterprise clients is time in draft mode. I hope to get bandwidth to run experiments here to ensure we are offering the quickest permissions configuration experience on the market.